- Notizie
Subscribe to our newsletter to receive the same news by email:
New features
We added 21 new languages to the Welcome Screen: Albanian, Armenian, Basque, Bengali, Bulgarian, Estonian, Galician, Icelandic, Japanese, Kazakh, Korean, Latvian, Malay, Norwegian Nynorsk, Polish, Serbian, Slovak, Swahili, Thai, Ukrainian, and Vietnamese.
Some of these languages only have little of our custom Tails applications translated, but other applications included in Tails are better translated.
If you want to translate Tails better in these languages or translate Tails into other languages, you can contribute to the Tor Project Weblate.
New languages will be included automatically in future versions of Tails as soon as 25% of strings are translated.
Changes and updates
Update Tor Browser to 13.0.14.
Update the Tor client to 0.4.8.11.
Rename the localization section of the Welcome Screen as Language and Formats.
Make Upgrade later the default option in the dialog opened by Tails Upgrader.
Include more errors in the detection of read and write errors on the USB stick.
Fixed problems
Fix a reliability issue that disabled Wi-Fi on some hardware. (#20045)
Disable SysRq keys, which allowed crashing a Tails session from the keyboard and bypass the lock screen. (#20334)
Disable Speculative Store Bypass to improve our mitigation of Spectre v4. (#20335)
Improve the error message when creating a Persistent Storage is impossible. (#20328)
For more details, read our changelog.
Get Tails 6.2
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 or later to 6.2.
You can reduce the size of the download of future automatic upgrades by doing a manual upgrade to the latest version.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.2 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.2 directly:
Changes and updates
Update Tor Browser to 13.0.13. This includes the changes brought by 13.0.12.
Update Thunderbird to 115.9.0.
Fixed problems
Fix Onion Circuits. #20233
Fix Welcome Screen frequently showing a "Welcome to Tails!" is not responding error. #20236
Fix Videos showing an error message during playback. #20243
Fix problems with changing the passphrase of the Persistent Storage. #20217
Tails Cloner can now install and upgrade to devices with multiple mounted partitions. #20149
The Persistent Storage settings now display all enabled custom Persistent Storage features. #19267
Mitigate the RFDS Intel CPU vulnerabilities. #20274
For more details, read our changelog.
Get Tails 6.1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 6.0 to 6.1.
You can reduce the size of the download of future automatic upgrades by doing a manual upgrade to the latest version.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails 6.1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.1 directly:
Highlights
Despite the bonus day this year, February flew by pretty quickly! Here's what we were up to:
We ended February more resilient and collaborative than when we started. We have new tooling to make it easier to work on shared documents, and use XMPP more effectively. We also worked to strengthen our front-end services and set up the back-end infrastructre to build redundancies into our services.
In 2021 and 2022, our usability tests with human rights defenders in Mexico and Brazil prompted several improvements in the installation instructions for Tails. Fixing 16 of the identified usability issues were remaining, and we fixed them all this month. These tests, experiences, and improvements will greatly shape our future trainings.
We finished updating our website for Tails 6.0. Check out the rewritten recommendation on secure deletion.
Releases
Tails 6.0 is the first version of Tails based on Debian 12 ("bookworm"), and is the sexiest, slickest, and sleekest Tails yet. It brings:
several important security updates: more robust error detection for the Persistent Storage, protections against malicious USB devices, and Diceware word lists in Catalan, German, Italian, Portuguese, and Spanish
some more usability features: new light modes—dark, night, and a combination of both; easier screenshoting and screencasting; and easier Gmail configuration in Thunderbird
and, updated version of most of the applications in Tails
To know more, check out the Tails 6.0 release notes and the changelog. Thank you to everyone who helped us out by testing the release candidate.
Metrics
Tails was started more than 806,714 times this month. That's a daily average of over 27,817 boots.
We are very excited to present you Tails 6.0, the first version of Tails based on Debian 12 (Bookworm) and GNOME 43. Tails 6.0 brings new versions of most of the software included in Tails as well as several important security and usability improvements.
New features
Error detection on the Persistent Storage
Tails 6.0 warns you about errors when reading or writing from your Tails USB stick.
These alerts can help you diagnose hardware failures on your USB stick and backup your Persistent Storage before it's too late.
Mount external devices automatically
When you plug in an external storage device, a USB stick or an external hard disk, Tails 6.0 mounts it automatically. If the storage device contains an encrypted partition, Tails 6.0 offers you to unlock the encryption automatically.
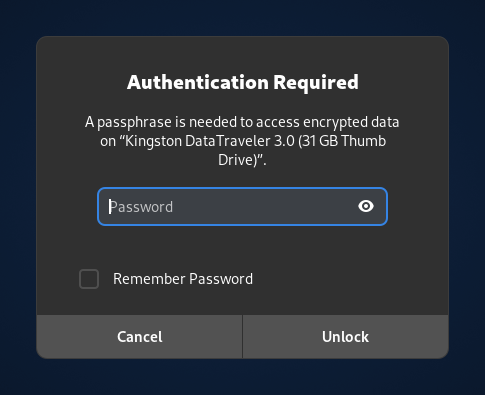
This feature also simplifies how to unlock VeraCrypt encrypted volumes.
Protection against malicious USB devices
If an attacker manages to plug a malicious USB device in your computer, they could run software that breaks the security built in Tails without your knowledge.
To protect from such attacks while you are away from your computer, Tails 6.0 ignores any USB device that is plugged in while your screen is locked.
You can only use new USB devices if they are plugged in while the screen is unlocked.
Dark Mode and Night Light
From the system menu of Tails 6.0, you can now switch between:
The default light mode with colder colors and more brightness
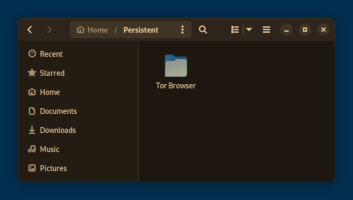
A dark mode
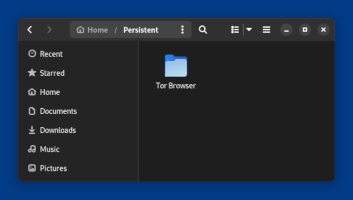
A night light mode with warmer colors and less brightness
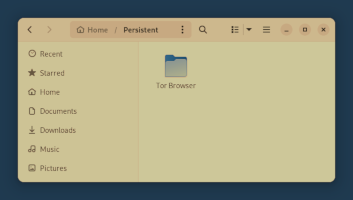
A combination of both the dark mode and night light mode
Easier screenshots and screencasts
GNOME 43 introduces a new ![]() shortcut in the system menu that makes it easier
to take a screenshot or record a screencast.
shortcut in the system menu that makes it easier
to take a screenshot or record a screencast.
Easier Gmail in Thunderbird
Thanks to changes in both Thunderbird and Gmail, it's much easier to configure a Gmail account in Thunderbird in Tails 6.0.
You don't have to configure anything special in your Gmail account, other than the usual 2-Step Verification.
You can sign in to your Gmail account directly when configuring it in Thunderbird.
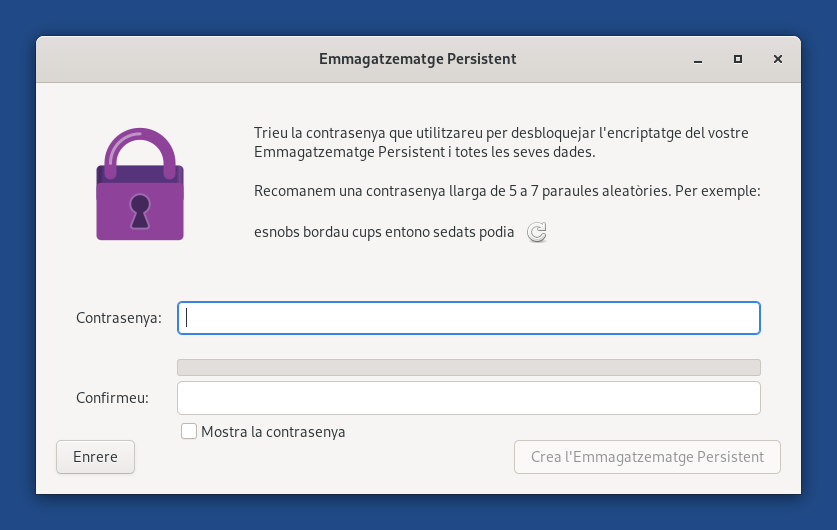
Diceware passphrases in 5 more languages
When creating a Persistent Storage, suggested passphrases are now also generated in Catalan, German, Italian, Portuguese, and Spanish.
Thanks to jawlensky who created the word lists for
Catalan, Italian, and Spanish for Tails, but also made them available to all
users of diceware.
Changes and updates
Included software
Tails 6.0 updates most of the applications included in Tails, among others:
Tor Browser to 13.0.10.
Electrum from 4.0.9 to 4.3.4
- Improve support for the Lightning protocol and hardware wallets.
KeePassXC from 2.6.2 to 2.7.4
- Add entry tags.
- Support dark mode.
- Redesign history view.
Metadata Cleaner from 1.0.2 to 2.4.0
- Redesign the whole user interface.
- Support dark mode.
- Add support for AIFF and HEIC files.
Text Editor from
gedittognome-text-editor- Support dark mode.
Inkscape from 1.0.2 to 1.2.2
Audacity from 2.4.2 to 3.2.4
Gimp from 2.10.22 to 2.10.34
Kleopatra from 4:20.08 to 4:22.12
Removed features
Remove the icons on the desktop.
The extension of GNOME Shell that we used to provide this feature is not well integrated into GNOME and created other problems. (#19920)
Remove the item Wipe and Wipe available disk space from the shortcut menu of the Files browser.
Secure deletion is not reliable enough on USB sticks and Solid-State Drives (SSDs) for us to keep advertising this feature.
We updated our documentation on secure deletion to new recommendations: use encrypted volumes, overwrite the entire device, or disintegrate it physically.
Remove the item Remove metadata from the shortcut menu of the Files browser.
The developers of MAT2, the metadata removal library used by Metadata Cleaner are not providing this option anymore.
Remove GtkHash
You can still install GtkHash as Additional Software.
Fixed problems
- Fix several issues with special characters and non-Latin scripts in the screen keyboard. (#18076)
For more details, read our changelog.
Known issues
Onion Circuits incorrectly claims Tor is not connected. (#20233)
The Welcome Screen sometimes displays a warning: "Welcome to Tails!" is not responding. (#20236)
If you see this warning, click on the Wait button.
Playing a video displays an error: Failed to query: In service 'dbus:org.freedesktop.Tracker3.Miner.Files': Unit tracker-miner-fs-3-service is masked. (#20237)
If you see this warning, click on the OK button.
OnionShare is still included as version 2.2.
We tried to include OnionShare 2.6 in Tails 6.0, but it has several issues that had security implications. (#20135 and #20140)
Mounting external devices automatically interferes with the Back Up Persistent Storage utility. (#20143)
Get Tails 6.0
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are only available from Tails 6.0~rc1 to 6.0.
All other users have to do a manual upgrade.
To install Tails 6.0 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 6.0 directly:
Highlights
Help us test Tails 6.0! A release candidate of the upcoming Tails 6.0 is out. Tails 6.0 promises to have a lot of exciting upgrades and new features. You can help us by testing the release candidate. We welcome your feedback by February 18 to either:
- tails-testers@boum.org (public mailing list), or
- tails-support-private@boum.org (private email)
It is all hands on deck for Tails 6.0! We have been upgrading Tails to Debian 12 ("bookworm"). We were also busy updating all our documentation to be ready for Tails 6.0. 1378 edited lines of HTML and Markdown code later, the documentation for Tails 6.0 is almost ready.
We were in the media! Here's @sajolida riffing with our long-time illustrator and comrade Anhdres about all things Tails. And here's @groente in conversation with Software Engineering Daily about how we interpret our values and mission in light of the various use cases of Tails.
Releases
Tails 5.22 was our first release of 2024! In Tails 5.22:
we continued improving the Persistent Storage:
- Tails now tries to repair the Persistent Storage if it is broken when you unlock it.
- Tails now does not try to unlock or delete a Persistent Storage that's on a read-only USB stick.
you can now download and upload files using Tor Browser to/from more folders.
we introduced more robust error messages when installing Tails with Tails Cloner. Thanks again to @BenWestgate for the efforts to improve Tails Cloner!
Metrics
Tails was started more than 806,263 times this month. That's a daily average of over 26,008 boots.
We are very excited to present you a release candidate of the upcoming Tails 6.0.
We plan to release Tails 6.0 officially on February 27. You can help us by testing already a release candidate of Tails 6.0 before February 18.
Tails 6.0 will be the first version of Tails based on Debian 12 (Bookworm) and GNOME 43. It will bring new versions of most of the software included in Tails as well as several important security and usability improvements.
We will provide security upgrades for Tails 6.0~rc1 like we do for regular versions of Tails.
New features
Mount external devices automatically
When you plug in an external storage device, a USB stick or an external hard disk, Tails 6.0~rc1 mounts it automatically. If the storage device contains an encrypted partition, Tails 6.0~rc1 offers you to unlock the encryption automatically.

Protection against malicious USB devices
If an attacker manages to plug a malicious USB device in your computer, they could run software that breaks the security built in Tails without your knowledge.
To protect from such attacks while you are away from your computer, Tails 6.0~rc1 ignores any USB device that is plugged in while your screen is locked.
You can only use new USB devices if they are plugged in while the screen is unlocked.

Dark Mode and Night Light
From the system menu of Tails 6.0~rc1, you can now switch between:
The default light mode with colder colors and more brightness

A dark mode

A night light mode with warmer colors and less brightness

A combination of both the dark mode and night light mode

Easier screenshots and screencasts
GNOME 43 introduces a new ![]() shortcut in the system menu that makes it easier
to take a screenshot or record a screencast.
shortcut in the system menu that makes it easier
to take a screenshot or record a screencast.

Easier Gmail in Thunderbird
Thanks to changes in both Thunderbird and Gmail, it's much easier to configure a Gmail account in Thunderbird in Tails 6.0~rc1.
You don't have to configure anything special in your Gmail account, other than the usual 2-Step Verification.
You can sign in to your Gmail account directly when configuring it in Thunderbird.

Diceware passphrases in 5 more languages
When creating a Persistent Storage, suggested passphrases are now also generated in Catalan, German, Italian, Portuguese, and Spanish.
Thanks to jawlensky who created the word lists for Catalan,
Italian, and Spanish for Tails, but also made them available to all users of
diceware.

Changes and updates
Included software
Tails 6.0~rc1 updates many of the applications included in Tails, among others:
Electrum from 4.0.9 to 4.3.4
- Improve support for the Lightning protocol and hardware wallets.
KeePassXC from 2.6.2 to 2.7.4
- Add entry tags.
- Support dark mode.
- Redesign history view.
Metadata Cleaner from 1.0.2 to 2.4.0
- Redesign the whole user interface.
- Support dark mode.
- Add support for AIFF and HEIC files.
OnionShare from 2.2-3 to 2.6-5
- Redesign the whole user interface.
- Allow creating chat rooms.
- Allow hosting static websites.
Text Editor from
gedittognome-text-editor- Support dark mode.
Inkscape from 1.0.2 to 1.2.2
Audacity from 2.4.2 to 3.2.4
Gimp from 2.10.22 to 2.10.34
Kleopatra from 4:20.08 to 4:22.12
Removed features
Remove the item Remove metadata from the shortcut menu of the Files browser.
The developers of MAT2, the metadata removal library used by Metadata Cleaner are not providing this option anymore.
Remove the item Wipe and Wipe available disk space from the shortcut menu of the Files browser.
Secure deletion is not reliable enough on USB sticks and SSDs for us to keep advertising this feature. We are still discussing which alternatives to explain in our documentation on secure deletion. (#19121)
Remove GtkHash
You can still install GtkHash as Additional Software.
Fixed problems
- Fix several issues with special characters and non-Latin scripts in the screen keyboard. (#18076)
Changelog
For more details about what has changed in Tails 6.0~rc1, read our changelog.
Known issues
Tails 6.0~rc1 is not reliably reproducible (#20165, #20166).
OnionShare 2.6 has several issues in Tails and Debian 12 (Bookworm) in general that have security implications:
OnionShare stays open in the background and fails to reopen. (#20135)
OnionShare crashes when stopping and restarting file shares in OnionShare. (#20140)
Despite the very interesting new features in OnionShare 2.6, we are considering keeping OnionShare 2.2 in Tails 6.0 because of these issues.
Mounting external devices automatically interferes badly with some other features:
The pointer doesn't change into a spinner anymore in some cases when launching applications. (#19920)
Send us feedback
Keep in mind that this is a test image. We tested that it is not broken in obvious ways, but it might still contain undiscovered issues.
Please, report any new problem before February 18 to either:
tails-testers@boum.org (public mailing list)
tails-support-private@boum.org (private email)
Get Tails 6.0~rc1
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are not available to 6.0~rc1.
You have to do a manual upgrade.
You will be able to automatically upgrade from 6.0~rc1 to 6.0 when it is released.
To download 6.0~rc1
Direct download
For USB sticks (USB image) (OpenPGP signature)
For DVDs and virtual machines (ISO image) (OpenPGP signature)
BitTorrent download
For USB sticks (USB image)
For DVDs and virtual machines (ISO image)
To install Tails 6.0~rc1 on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
New features
In Tor Browser, you can now save files to more folders: Documents, Downloads, Music, Pictures, and Videos. You can also upload files from these folders.
When your Persistent Storage is broken, Tails now tries to repair its file system when you unlock it in the Welcome Screen.
Changes and updates
Report the write speed after cloning a Persistent Storage from Tails Cloner.
Do not try to unlock or delete a Persistent Storage on a read-only USB stick.
Update Tor Browser to 13.0.9.
Update Thunderbird to 115.7.
Fixed problems
Stop leaking the first-level domain of visited websites in WhisperBack reports. The problem was first introduced in Tails 5.15.1 (July 2023). (!1344)
Make installing Tails with Tails Cloner more robust by fixing occasional errors
AttributeError: 'NoneType' object has no attribute 'props'. Thanks to Ben Westgate! (!1312)Fix saving the Additional Software configuration when creating a Persistent Storage. (!1350)
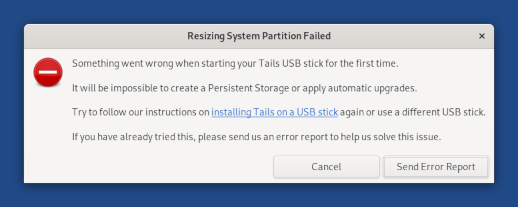
Fix help link when resizing the system partition fails the first time Tails is started. (!1341)
For more details, read our changelog.
Get Tails 5.22
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 5.0 or later to 5.22.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails on a new USB stick
Follow our installation instructions:
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 5.22 directly:
Happy 2024, Tails-y folks! We wish you a year full of nourishing energies, forceful resistance, and great health ✊🏽
Highlights
2023 was an eventful year at Tails. We kicked off the 1st year of our 3-year strategic plan with 16 releases of Tails, significant improvements to core Tails features like the new Persistent Storage, and researched cool, new features we want to bring to you. In parallel, we started moving into a new home and made investments to become a more sustainable project and a healthier workplace. Read more about 2023 at Tails here. If you'd rather listen, check out our presentation at State of the Onion 2023!
We are raising funds for our work in 2024 but our annual fundraising campaign has fallen short of our goal. So, we've extended our fundraiser till January 20, 2024. If you find our work useful and can contribute, we'd appreciate your help. Every contribution, no matter the size, makes a big difference. Donate now!
Talking about contributions that make a difference, we remain ever so grateful to our sponsors! Last month, wordsolver.co renewed their sponsorship of Tails. This is the 3rd year of their support for Tails' mission! Thank you 💜
Releases
We released Tails 5.21. In 5.21:
Tor client and Tor Browser are up-to-date
we improved Tails's handling of date and time: you'll find localised dates in the top navigation, and separately, we replaced the unpunctual web servers in our htpdate pool
the backup feature of Tails Cloner is friendlier to use. Thanks @BenWestgate!
And lots more.
Metrics
Tails was started more than 815,559 times this month. That's a daily average of over 26,300 boots.
Changes and updates
Help troubleshoot when resizing the system partition fails the first time Tails is started.
Translate the date displayed in the top navigation bar.
Update Tor Browser to 13.0.7.
Update the Tor client to 0.4.8.10.
Fixed problems
Fix Tor Browser crashing when clicking on the UBlock icon. (#20061)
Make time synchronization more reliable. (#19923)
@BenWestgate fixed several issues in the backup feature of Tails Cloner:
For more details, read our changelog.
Get Tails 5.21
To upgrade your Tails USB stick and keep your Persistent Storage
Automatic upgrades are available from Tails 5.0 or later to 5.21.
You can reduce the size of the download of future automatic upgrades by doing a manual upgrade to the latest version.
If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a manual upgrade.
To install Tails on a new USB stick
Follow our installation instructions:
- Install from Windows
- Install from macOS
- Install from Linux
- Install from Debian or Ubuntu using the command line and GnuPG
The Persistent Storage on the USB stick will be lost if you install instead of upgrading.
To download only
If you don't need installation or upgrade instructions, you can download Tails 5.21 directly:
Malicious actors upped the ante in 2023.
I cosiddetti sistemi di intelligenza artificiale sono diventati molto popolari, alimentando la [disinformazione] politica (https://www.wired.com/story/slovakias-election-deepfakes-show-ai-is-a-danger-to-democracy/). programmi. Le chiusure e i rallentamenti di Internet sono diventati saldamente radicati negli strumenti autoritari per censurare i discorsi progressisti. E le continue rivelazioni di attacchi zero-click hanno evidenziato la pericolosa onnipotenza del complesso militare-digitale.
But, we also made plans to call their ante.
Abbiamo costruito una strategia triennale all'avanguardia per fare di Tails un avversario formidabile per queste potenti forze repressive. Abbiamo pianificato di comprendere meglio l'uso di Tails da parte di giornalisti e attivisti e di comprendere e migliorare l'uso di Tails nella [maggioranza del mondo ] (https://www.harvarddesignmagazine.org/articles/shahidul-alam-on-the-majority-world/). Tutto questo introducendo nuove funzionalità e migliorando quelle esistenti per rendere Tails ancora più rilevante.
Here's the progress we made in the first year of the plan.
Product development
The Persistent Storage got even better at storing encrypted data.
Tails 5.8 è stato uno dei rilasci di Tails più importanti degli ultimi anni. In Tails 5.8 abbiamo presentato un nuovo Archivio Persistente. Il nuovo Archivio Persistente non richiede il riavvio dopo che lo hai creato o ogni volta che attivi una nuova funzionalità. Inoltre, ha reso più facile la persistenza di un maggior numero di impostazioni. Ciliegina sulla torta: un elegante restyling per l'Archivio Persistente!
But the new Persistent Storage wasn't all fun and games for Tails users. It was buggy and we worked extra hard to fix the issues our users faced.
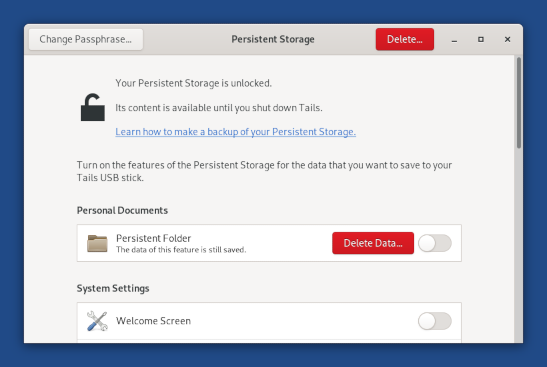
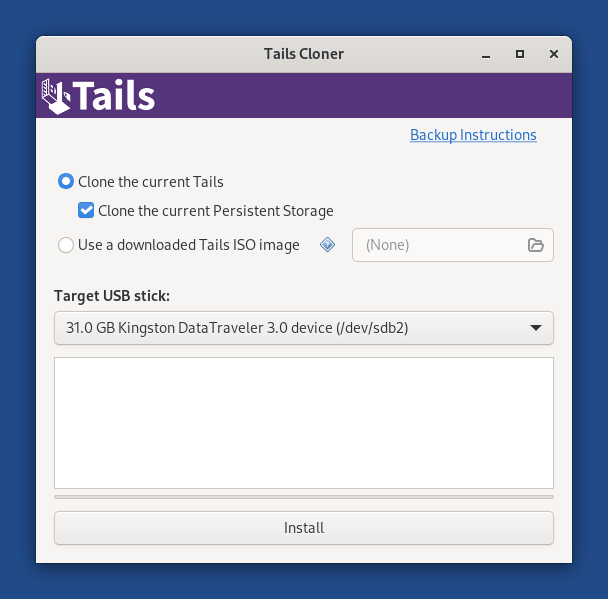
Non ci siamo fermati qui. Abbiamo anche continuato ad aggiungere funzionalità all' Archivio Persistente. Ora è più facile sia fare il ?backup dell'intero Archivio Persistente che ?cancellare i dati di una singola funzionalità.
 |
 |
Abbiamo anche introdotto migliori pratiche per la password in modo da proteggere l'Archivio Persistente. Le passphrase diceware generate casualmente e una struttura di crittografia aggiornata rendono il Archivio Persistente esponenzialmente più sicuro.

Improvements to the Tor Connection make it easier to circumvent censorship.
The Tor Connection Assistant is slicker. We improved the error messaging when connecting automatically to the Tor network and the handling of captive portals.
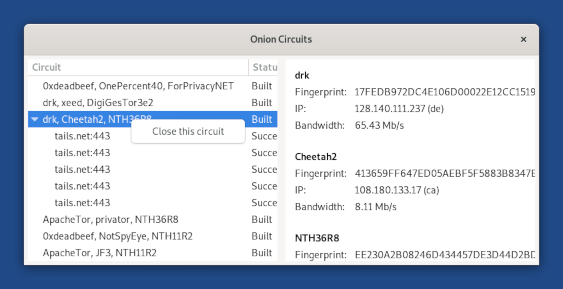
La connessione a Tor è solo una parte della storia. A volte, gli utenti di Tails possono trovarsi su circuiti Tor lenti. E peggio ancora, non riescono a risolvere i problemi. Per questo motivo, abbiamo reso più facile chiudere i fastidiosi circuiti Tor su cui a volte ci troviamo.
 |
Tails rimane uno dei sistemi operativi più sicuri al mondo.
Quest'anno abbiamo rilasciato 15 versioni di Tails, assicurando agli utenti l'ultima versione di Tor Browser e Thunderbird. Sì, QUINDICI!
We also asked Radically Open Security to do a security audit of Tails. Their findings affirmed our cutting-edge security.
PS: Keeping Tails updated is your best defense against online surveillance and censorship!
And we started moving to our new home!
🎉 ✨ tails.net ✨ 🎉
Abbiamo completato una serie di progetti di miglioramento della home. Per rendere la nostra nuova home ancora più accogliente per chi parla lingue diverse, abbiamo revisionato il commutatore di lingue. Abbiamo appena aggiunto anche le traduzioni in catalano. Gràcies per ser aquí!
High footfall areas of the website got a new carpet too. Check out our new Contribute, Support, and Contact us pages.
A huge shout-out to the volunteers who made these possible: @jawlensky for the website redesign and to our Catalan translations team!
Community and organizational health
Sprint. Il nostro team principale ha organizzato 2 sprint quest'anno. Verso Pasqua, ci siamo riuniti a Parigi. L'ordine del giorno era la stesura del bilancio dell'anno successivo e la costruzione di una tabella di marcia verso la salute finanziaria. All'ordine del giorno c'erano anche: formaggio francese, snack indiani piccanti e [Dixit] (https://boardgamegeek.com/boardgame/39856/dixit). Più tardi, nel corso dell'anno, ci siamo incontrati di nuovo in un mix di partecipazione online e di persona. Abbiamo riflettuto sugli sforzi compiuti quest'anno e abbiamo elaborato piani per un futuro più sostenibile del progetto.
Riflessioni. Aspirando di raggiungere e incoraggiare popolazioni più diverse di utenti di Tails, abbiamo anche intrapreso un percorso per migliorare la diversità del progetto. Il nostro gruppo di lavoro ha iniziato a riunirsi quindicinalmente per riflettere sulle nostre norme sul posto di lavoro. Stiamo usando questo testo del Centre for Community Organizations come guida alla riflessione e al miglioramento.
Financial health
Malicious actors are not going to buckle down, but neither are we. This year, Tails was instrumental in several high-risk investigations and struggles for progressive change. Like this damning indictment of the Mexican army's systematic surveillance of feminists in the country.
I, (@bokonon), joined our small team at Tails this year, to lead our fundraising activities. I have been obsessing over how a free software project like ours can continue improving Tails while keeping it free. And one thing is already clear: we will need your help. Often.
While we don't know how many Tails users donate to Tails, our guess is ~1%. Tails is designed for use by people living vulnerable, high-risk lives. Many of whom are likely to not be in a position to contribute. Your donations keep Tails free for everybody else!
We are near the end of our campaign to fund Tails in 2024, but quite a way off our goals.
We might never have the resources that powerful, malicious actors do, but we know one thing: together, we can punch much above our weight. As we go into the holidays, join us in ensuring that the Internet does not become synonymous with surveillance and censorship. Give the gift of privacy today!