- doc
- anonymous internet
- Conectando à rede Tor
Tudo que você faz na internet a partir do Tails passa pela rede Tor.
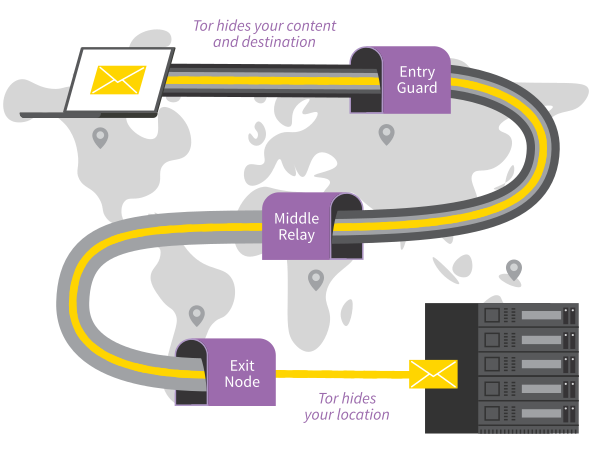
Tor criptografa e anonimiza suas conexões ao passá-las por 3 "relays" (servidores de repetição) aleatórios diferentes. Os relays do Tor são servidores operados por diferentes pessoas e organizações em todo o mundo.
You cannot access the Internet from Tails until you are connected to
Tor. For example, Tor Browser displays the error message Proxy server
refusing connections until you are connected to Tor.
Pelo fato do Tor rotear seu tráfego de internet por 3 retransmissores antes de atingir seu destino, a conexão é mais lenta do que quando você não usa Tor.
Veja nossa documentação em [porque o Tor é lento|doc/anonymous_internet/tor/slow]].
Para se conectar à rede Tor:
Conecte-se a uma rede local, cabeada, Wi-Fi, ou móvel.
O assistente de Conexão Tor aparece para te ajudar com a conexão à rede Tor.
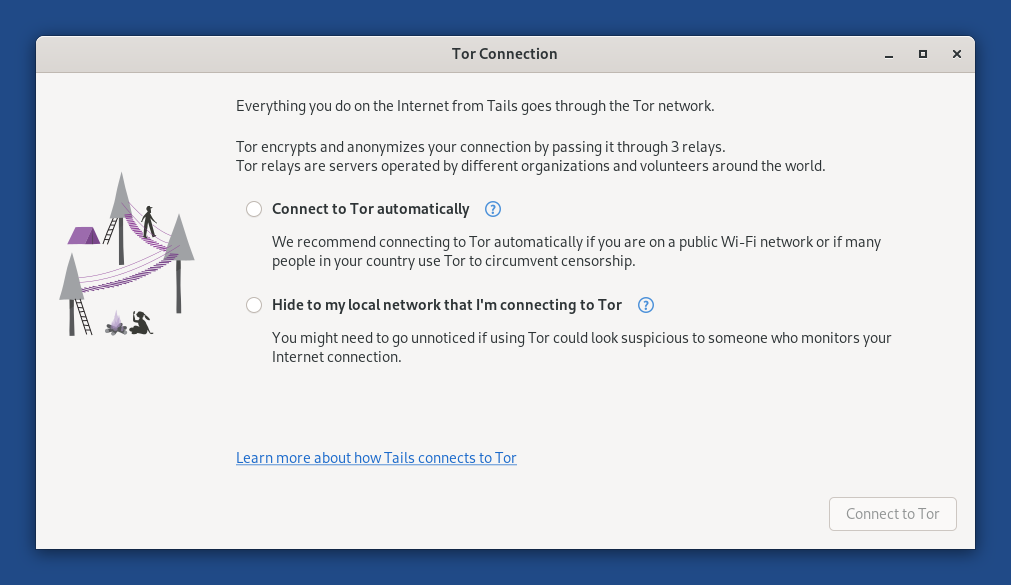
Escolha se você quer:
Conectar à rede Tor automaticamente
Esconder da sua rede local que você está conectado à rede Tor
As implicações de ambos os métodos estão detalhadas abaixo.
Retransmissores e pontes na rede Tor
Retransmissores públicos do Tor
Na maior parte do tempo, sua rede local não bloqueia o acesso à rede Tor e você pode usar um retransmissor público como seu primeiro retransmissor do Tor.
Ao usar um relay público para entrar na rede Tor, qualquer análise simples do tráfego de dados na sua rede local permite concluir que você está se conectando à rede Tor, mas sua atividade online se manterá segura e anônima.
Pontes para a rede Tor
Pontes Tor são retransmissores secretos do Tor usados para esconder a sua conexão à rede Tor.
Use uma ponte como seu primeiro retransmissor caso existam na sua rede bloqueios para conexão à rede Tor, ou então caso o mero uso da rede Tor possa levantar suspeitas para alguém que esteja monitorando sua conexão à Internet.
A tecnologia usada pelas pontes Tor é feita para driblar a censura em lugares onde conexões à rede Tor são bloqueadas, como por exemplo em alguns países que praticam censura pesada, em algumas redes públicas, ou em redes com alguns tipos de controle parental.
Isso é feito camuflando sua conexão para que ela não seja reconhecida como uma conexão à rede Tor. Por isso, essa mesma tecnologia pode ser usada para esconder o fato de que você está usando Tor, caso isso possa parecer suspeito para alguém que monitore sua conexão a internet.
Pontes Tor são menos confiáveis e mais lentas que relays públicos do Tor.
Conectando automaticamente à rede Tor
Recomendamos a conexão automática à rede Tor se você estiver em uma rede Wi-Fi pública ou se varias pessoas no seu país usam Tor para driblar a censura.
Quando você escolhe esta opção:
Primeiro, o Tails sincroniza automaticamente o relógio do computador, porque a informação correta de data e hora é imprescindível para que seja possível conectar à rede Tor.
O Tails descobre a data e hora corretas conectando ao serviço de detecção de portal cativo do Fedora, que é usado pela maioria das distribuições Linux. Esta conexão não passa pela rede Tor e é uma exceção à nossa política de somente realizar conexões à Internet através da rede Tor.
Você pode saber mais sobre a nossa avaliação de segurança dessa sincronização de data e hora na nossa [[documentação de projeto sobre tráfego por fora do Tor|contribute/design/Tor_enforcement#non-tor-traffic.
Se ao invés disso você quiser esconder o fato de que está conectando à rede Tor, talvez você precise acertar o relógio do computador manualmente.
Caso o Tails não consiga sincronizar o relógio porque antes você precisa entrar na rede usando um portal cativo, uma tela de erro será mostrada pra te ajudar a fazer isso.
Para instruções detalhadas, veja como entrar em uma rede usando um portal cativo.
Em seguida, o Tails tenta de diferentes maneiras conectar à rede Tor até que tenha sucesso:
Tails tenta se conectar à rede Tor diretamente usando retransmissores públicos, sem usar uma ponte.
Tails tenta se conectar à rede Tor usando uma das pontes padrão, já inclusas no Tails, caso falhe em conectar usando retransmissores públicos.
Tails uses the default obfs4 bridges from Tor Browser.
Se os retransmissores públicos e as pontes padrão não funcionarem, o Tails pedirá para que você configure uma ponte personalizada.
Alguém que esteja monitorando sua conexão à Internet poderia identificar que essas tentativas estão vindo de um usuário do Tails.
Escondendo da sua rede local que você está conectado à rede Tor
Talvez você não queira que te notem caso o uso do Tor possa levantar suspeitas para alguém que esteja monitorando sua conexão à Internet.
Ao escolher essa opção, Tails apenas conectará à rede Tor depois que você configurar uma ponte. Pontes são retransmissores secretos da rede Tor que escondem o fato de que você está conectando à rede Tor.
É impossível esconder dos sites que você visita o fato de que você está usando Tor, pois a lista de nós de saída da rede Tor é pública.
Nosso time está fazendo o possível para te ajudar a conectar à rede Tor usando os tipos de ponte menos chamativos. Por isso, quando você decide esconder o fato de que está se conectando à rede Tor:
O Tails não detecta automaticamente se é ou não necessário entrar na rede usando um portal cativo.
Pontes padrão não estão disponíveis.
Você terá que saber o endereço de uma ponte personalizada.
Para solicitar uma ponte personalizada, você pode:
Pedir uma ponte em https://bridges.torproject.org/.
Recomendamos que você faça isso antes de iniciar o Tails, idealmente a partir de uma rede local diferente da que você deseja esconder o fato que está usando Tor.
Envie um email vazio para bridges@torproject.org a partir de um endereço de email do Gmail ou do Riseup.
Você pode, por exemplo, enviar um email a partir do seu celular e depois digitar a ponte no Tails.
Enviando o email, você revela para o Gmail ou para o Riseup que você está tentando se conectar à rede Tor, mas não para alguém que esteja monitorando sua conexão à Internet.
Mesmo que alguém saiba qual ponte você está usando, não pode saber o que você está fazendo online a partir do Tails.
Você pode usar apenas os tipos de ponte que o nosso time considera suficientemente discretas.
No Tails, atualmente apenas pontes obfs4 escondem o fato que você está usando Tor.
Para salvar o endereço da última ponte que conseguiu conectar à rede Tor com êxito, ative a funcionalidade Pontes Tor do Armazenamento Persistente.
No futuro, tornaremos mais fácil a utilização de pontes personalizadas:
Visualizando o estado do Tor
O estado do Tor aparece como um ícone de cebola na área de notificações:
?tor-status.png
 Você está com conexão à rede Tor.
Você está com conexão à rede Tor. Você não está com conexão à rede Tor.
Você não está com conexão à rede Tor.
Resolvendo problemas com a conexão à rede Tor
Veja nossa documentação sobre resolução de problemas de conexão à rede Tor.
